Demystifying AWS VPC Key Concepts.
In this post I try my best to cover AWS VPC key concepts
What is VPC

VPC stands for virtual private cloud, which allows the hosting of AWS resources in a logically isolated virtual network.
By default, AWS provides a default Virtual Private Cloud (VPC) in each region. This is the reason why we can directly start an EC2 instance, enabling users to quickly launch and run EC2 instances without having to manually set up networking components.
CIDR
Classless Inter-Domain Routing is a key concept behind VPC subnetting and for network isolation. This helps to allocate the IPs efficiently.
Subnetting: CIDR enables subnetting, which involves dividing a larger network into smaller subnetworks or subnets. Each subnet has its own network prefix, allowing for better organization and management of IP addresses within a network.
IP Address Range Calculation: CIDR notation provides a concise and standardized way to represent IP address ranges. By specifying the network prefix, it becomes easier to calculate the range of IP addresses available within a given network.
The most commonly used internal IP address range is defined by the Internet Assigned Numbers Authority (IANA) and is known as IPv4 (Internet Protocol version 4) private address space. The IPv4 private address ranges are as follows:
10.0.0.0 to 10.255.255.255 (10.0.0.0/8), a range that provides up to 16 million unique IP addresses.
172.16.0.0 to 172.31.255.255 (172.16.0.0/12), providing about 1 million unique IP addresses.
192.168.0.0 to 192.168.255.255 (192.168.0.0/16), which offers about 65,000 unique IP addresses.
- In AWS, the largest CIDR block range you can allocate for a virtual private cloud (VPC) is a /16 CIDR block. A /16 CIDR block actually provides a total of 65,536 out of this total IPs AWS reserves 5 IP addresses within each subnet, the first four IP addresses in each subnet are reserved for network addressing purposes, and the fifth IP address is reserved for Amazon DNS resolution.
Subnet
In the context of AWS, a subnet is a range of IP addresses in a VPC. When you create a VPC, you can divide it into multiple subnets, each with its own IP address range. Subnets are typically associated with a specific availability zone (AZ) within an AWS region.
Here are a few key points about subnets in AWS:
IP Address Range: Each subnet has its own IP address range, which is a subset of the IP address range of the VPC. The IP address range is specified using CIDR notation, such as 10.0.0.0/24, indicating a subnet with 256 IP addresses.
Availability Zones: Subnets are associated with a specific availability zone within an AWS region. This allows for deploying resources in different availability zones to achieve high availability and fault tolerance.
Routing: Each subnet has its own route table, which controls the traffic flow within the subnet and between subnets. You can configure routing rules to direct traffic between subnets or to external networks.
Security: Subnets can be associated with security groups and network access control lists (NACLs) to control inbound and outbound traffic at the subnet level.
Purpose: Subnets are often used to logically separate different components or tiers of an application or system. For example, you might have separate subnets for web servers, application servers, and database servers.
Routing
Use route tables to determine where network traffic from your subnet or gateway is directed.
Route tables act as a rule book and direct the traffic internally between the subnets or to the internet.
A route table can be associated with multiple subnets. However, a subnet can only be associated with one route table at a time. Any subnet not explicitly associated with a table is implicitly associated with the main route table by default.
We can create one common route table and associate multiple common subnets with it.
What makes your subnet public or private?
This is one of the key questions we get when working with public and private subnets, here route table plays a crucial role in determining whether a subnet is public or private in AWS.
The Internet Gateway facilitates connectivity between a subnet and the Internet. However, simply creating and attaching the Internet Gateway to a subnet does not automatically make the subnet public. To make a subnet public, you need to configure the associated route table to direct all public IP traffic to the Internet Gateway.
Difference between Gateways and Endpoints
| Internet Gateway | VPC Endpoint |
| An Internet Gateway is a horizontally scalable, highly available AWS-managed service that enables communication between your VPC and the Internet. | A VPC Endpoint is a highly available and horizontally scalable service that allows you to establish a private connection between your VPC and AWS services, eliminating the need to access them over the public internet. |
| By attaching an Internet Gateway to your VPC, instances within the VPC can communicate with the Internet and be accessed from the Internet. | It allows secure and direct communication between your VPC and supported AWS services (such as S3, DynamoDB, or SNS) without the need for an internet gateway, NAT device, or public IP address. |
| An Internet Gateway serves as a gateway for Internet-bound traffic, allowing resources within the VPC to access the Internet or be accessed from the Internet. | With VPC endpoints, data between your VPC and the AWS service remains within the AWS network, improving security and reducing data transfer costs. |
| It performs network address translation (NAT), allowing instances in the VPC with private IP addresses to communicate with the internet using public IP addresses | VPC endpoints can be interface endpoints or gateway endpoints, depending on the AWS service you are connecting to. |
Transit gateways
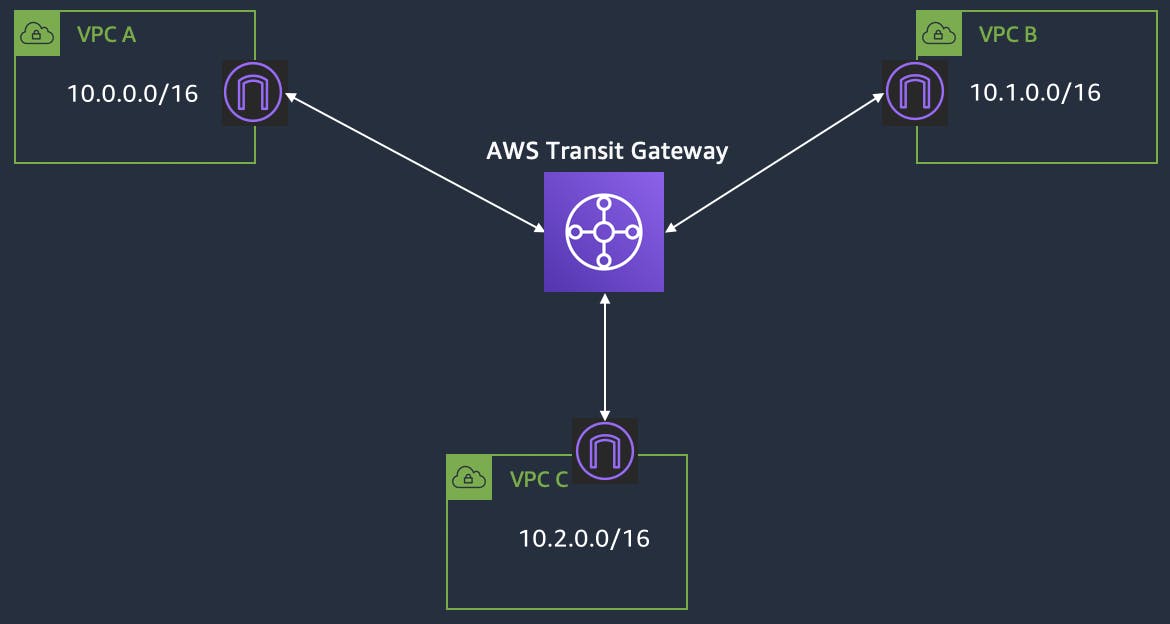
The transit gateway acts as a central hub, to route traffic between your VPCs, VPN connections, and AWS Direct Connect connections.
If we have 2 VPCs we can connect them by using VPC peering, but if we have more VPCs in order to peer multiple VPCs with each other, the number of connections would be based on the formula [n(n-1)/2]. For example, if you have a total of 5 VPCs in your network and all need peering then the total connections would be 10.
By using Transit gateways, we can consolidate and manage network routing and connectivity in a more efficient and scalable manner. Instead of maintaining the network routing for each VPC, we can manage at a single point.
NACLs and Security groups
| Security Groups: | Network Access Control Lists (NACLs): |
| Operate at the instance level (within a VPC) and are stateful. | Operate at the subnet level (within a VPC) and are stateless. |
| Control inbound and outbound traffic based on security group rules. | Control inbound and outbound traffic based on numbered rules. |
| Associate with instances and provide security at the protocol and port level. | Apply to all instances within the associated subnet. |
| Automatically allow outbound traffic for established connections. | Support allow and deny rules for both inbound and outbound traffic. |
Elastic IP
An Elastic IP (EIP) is a static, public IPv4 address that you can allocate and assign to your AWS resources such as EC2 instances, NAT gateways, or load balancers. Unlike the dynamic public IP addresses assigned by default to EC2 instances, an EIP remains associated with your AWS account until you release it.
Elastic IPs will not change until and unless you release them. So resources associated with elastic IPs will have the same IP address even after restarting.
NAT Gateway
The NAT Gateway is typically placed within a public subnet in your Amazon VPC. The NAT gateway allows private instances to connect internet but blocks the inbound connection from the network, It's a one-way communication.
By placing the NAT Gateway in a public subnet and configuring the appropriate routing, you enable instances in private subnets to access the internet for tasks such as installing external packages and performing upgrades, while effectively blocking incoming requests. This setup ensures a secure environment for private instances, allowing them to communicate with external resources as needed.
NAT gateways in AWS require an Elastic IP address (EIP) to function properly. An Elastic IP address is a static public IP address that you can allocate and associate with your NAT gateway.
So, when setting up a NAT gateway in AWS, ensure you have an available Elastic IP address to associate with it.
Bastion Host in AWS VPC

A bastion host is an EC2 instance that acts as a secure gateway to access private instances within an AWS VPC (Virtual Private Cloud) environment. It is a dedicated server that provides secure access to resources in the private network from outside the VPC.
We can follow agent forwarding for connecting to any instance that is using the same key pair, this is also known as SSH agent forwarding.
Conclusion:
These are the few key concepts that we need to understand in AWS VPC. Also, have attached some resources that I referred to my learning. Please let me know if I am missing anything.
